TrustedInstaller.exe is an official Microsoft process whose function is to manage Windows updates. However, it is frequently misidentified as a virus. It is somewhat understandable given that TrustedInstaller is infamous for heavy CPU consumption, and there have been instances where it has been taken over by malware, make sure you read this article to learn how to evaluate whether TrustedInstaller is a trusted friend or foe.
Windows is one of the world’s most popular operating systems, yet user and system issues can occasionally occur.
It may be the source of a Windows 10 computer’s high CPU consumption, sluggish response to commands, or lengthy starting time if you observe these symptoms.
TrustedInstaller.exe Is it a virus?
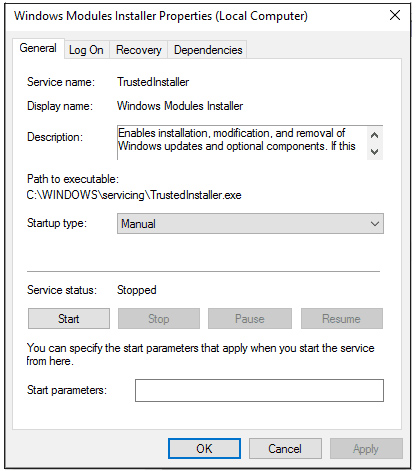
TrustedInstaller.exe is a Windows Modules Installer-related process and one of the essential Windows Resource Protection components.
It is included in every Windows version from Vista.
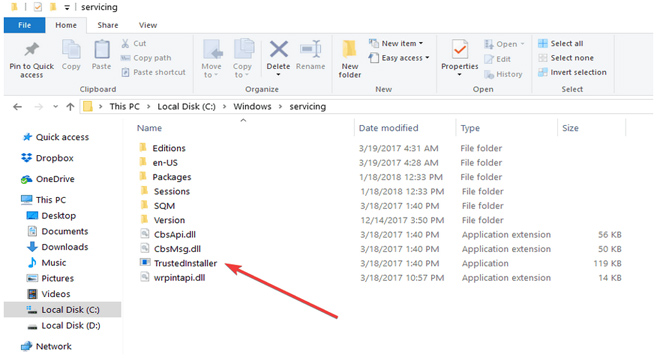
Its primary function is to install and change Windows updates and other system components that significantly impact your machine. It may be found under C:Windowsservicing and is typically between 100 and 200 KB in size.
Since TrustedInstaller is a legitimate Windows component, there is no need to uninstall or modify it. Typically, you won’t even notice it. Keep in mind that removing or changing it could result in Windows functionalities being inoperable, which could lead to more severe issues.
How can I fix TrustedInstaller?
Users claim that TrustedInstaller.exe renders their PCs inoperable. However, you must be aware that the process could be corrupted or even replaced by malware with the same name if you are in this situation.
Checking the CPU load is one approach to detecting TrustedInstaller malware. You may evaluate the performance of your CPU using InSpectre or a comparable tool. If TrustedInstaller.exe consistently uses a significant portion of your computer’s resources, you may be infected.
As an aside, the legitimate TrustedInstaller will consume a significant amount of system resources, but only during or after a Windows upgrade.
Checking the file’s location is another method for identifying malware.
As previously stated, the legitimate Windows component is located under C:Windowsservicing. If the location is different, you’re likely dealing with malware.
The TrustedInstaller malware is hazardous and can secretly access your camera and microphone. If you believe hackers can access your webcam, secure your privacy with this webcam protection software.
Replace TrustedInstaller with SFC scan
Suppose you cannot determine whether TrustedInstaller is a legitimate Windows process or malicious software. In that case, we suggest beginning with a System file check to ensure that your files are in order.
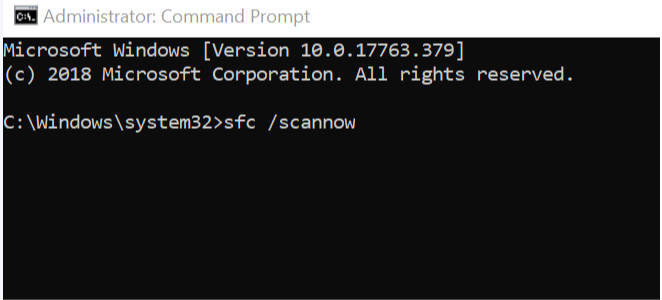
1. Type cmd in the Windows search box. Select Run as administrator by right-clicking the top result.
2. In the command prompt cmd window, type sfc /scannow, wait for the procedure to complete, and then restart the machine.
This procedure will fix faulty files, including TrustedInstaller, and afterward, everything should function normally.
If TrustedInstaller is a virus, it must be deleted immediately. You will need robust malware removal solutions such as Bitdefender to accomplish this.
Final Words
We hope the information about TrustedInstaller.exe has helped you comprehend what it is and how it operates. If you have any more questions, please submit them in the section below.